Spring Security secures your application through a chain of filters. Here’s a breakdown of the authentication process step-by-step, including the inbuilt filters and classes involved:
1. Request Intercepted:
- The request first hits the
FilterChainProxy. This component acts as a central point for managing all security filters.
2. CSRF Protection (Optional):
- If enabled, the
CsrfFilterchecks for Cross-Site Request Forgery (CSRF) attempts. It validates a CSRF token to prevent unauthorized actions.
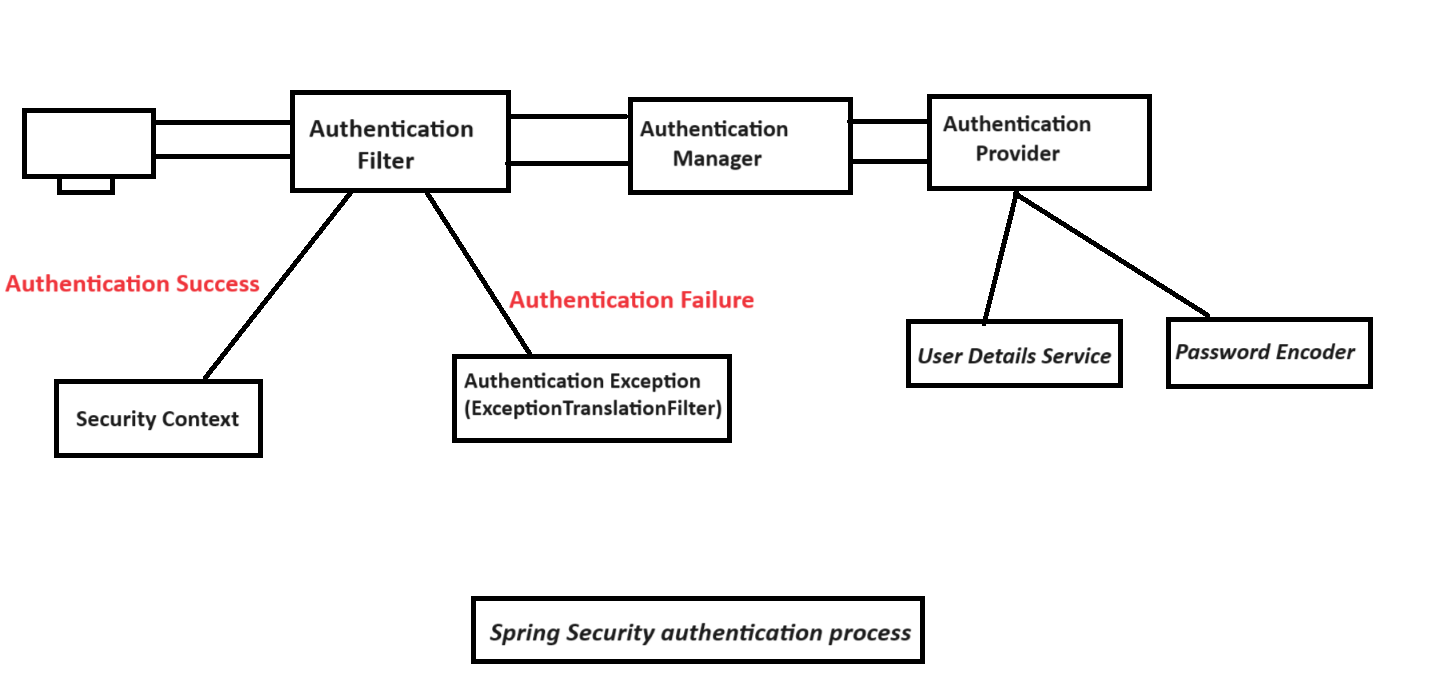
3. Authentication Filters:
- The
FilterChainProxythen invokes the configured authentication filters. Here are some common ones:UsernamePasswordAuthenticationFilter: This is the default filter that handles username and password login forms. It extracts credentials (username/password) from the request body and initiates the authentication process.BasicAuthenticationFilter: This filter handles Basic Authentication requests, where credentials are encoded in the Authorization header. It decodes the credentials and initiates authentication.RequestHeaderAuthenticationFilter: This filter can be used to extract credentials from custom request headers.SessionManagementFilter: This filter checks for a valid session and manages session creation/destruction as needed for authentication.
4. Authentication Provider Selection:
- Based on the chosen filter (e.g., UsernamePasswordAuthenticationFilter), the appropriate
AuthenticationProvideris selected. Common providers include:DaoAuthenticationProvider: This provider works with aUserDetailsServiceto load user information (username, password, authorities) from a data source like a database and verify the credentials against the loaded user.UserDetailsService(interface): This interface defines a method to load aUserDetailsobject containing user information for authentication. You’ll implement this interface to retrieve user details from your chosen data source.InMemoryUserDetailsManager(optional): This class allows you to define users in memory for testing purposes (not recommended for production).
5. Authentication Attempt:
- The
AuthenticationProvider(e.g., DaoAuthenticationProvider) calls theUserDetailsServiceto retrieve user details based on the provided credentials. - The retrieved
UserDetailsobject is then compared against the credentials supplied in the request.
6. Authentication Success:
- If the credentials match, an
Authenticationobject is created containing the authenticated user’s information (username, authorities).
7. Security Context Update:
- The
SecurityContextHolderstores the successfulAuthenticationobject, making it accessible throughout the application for authorization decisions.
8. Authorization (Optional):
- After successful authentication, the
FilterChainProxymight invoke authorization filters likeUrlSecurityExpressionFilterto check if the authenticated user has permission to access the requested resource based on URL patterns and user authorities.
9. Request Processing:
- If both authentication and authorization are successful, the request proceeds to the secured resource or controller method.
10. Authentication Failure:
- If authentication fails (wrong credentials, user not found, etc.), an
AuthenticationExceptionis thrown. TheExceptionTranslationFilterhandles this exception and might trigger mechanisms like redirecting to a login page or sending an unauthorized response.
This explanation covers the core inbuilt filters and classes involved in Spring Security’s authentication process. Remember that the specific filter chain and configuration can be customized based on your application’s security needs.
Leave a Reply