Authentication and authorization are two fundamental security concepts that work together to control access to systems and resources. They are often confused, but they serve distinct purposes:
What is Authentication ?
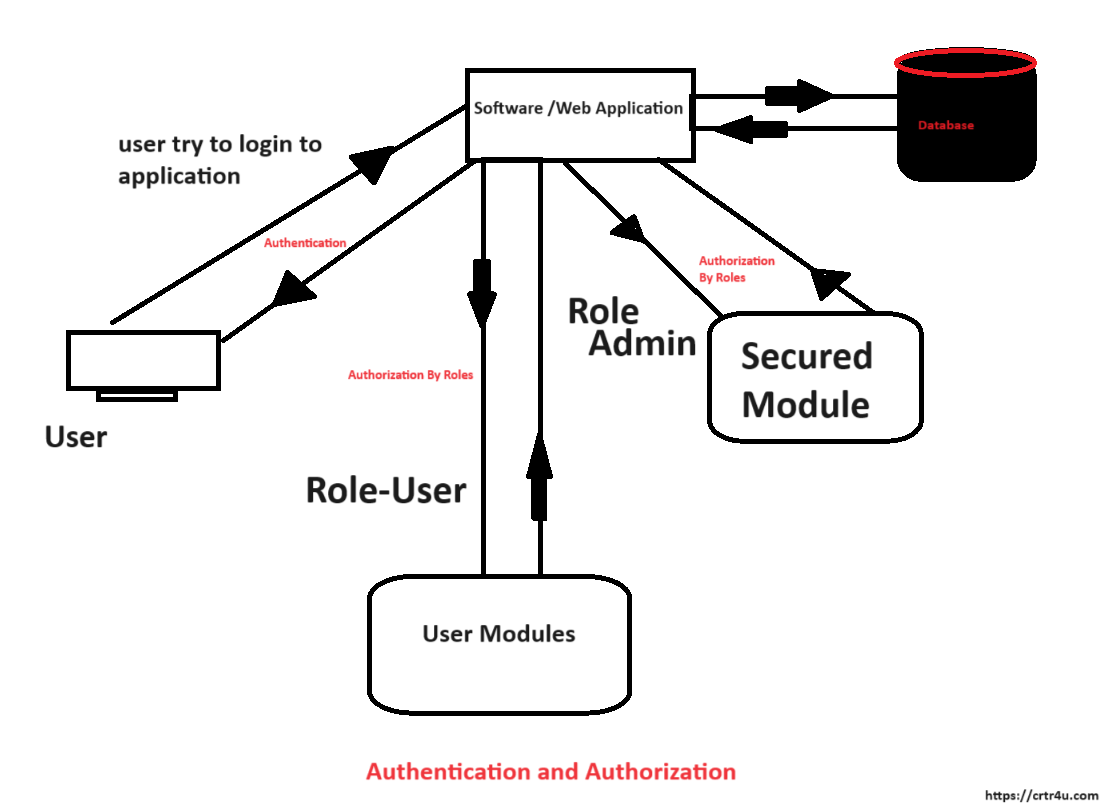
Authentication is the process of verifying a user’s identity. In simpler terms, it answers the question “Are you who you say you are?”. Imagine entering a building with security. You show your ID (proof of identity) to the guard, who checks it against a database (verification).When you enter username and password and click on login button , your username and password get verified in Database and if it is correct then only you are authenticated.
What is Authorization ?
Authorization determines what a user can do once their identity is verified. It answers the question “What are you allowed to access?”. Continuing the building analogy, after verifying your ID, the guard checks your access level (authorization) to see which floors you can enter. For Example Once you logged in to application successfully then based on your roles you can see different modules or screens , user can see only user related screens , while admin can see some additional screens ,this all happen because of Authorization.
Here’s a breakdown of the key differences:
Focus: Authentication – identity verification, Authorization – access rights
Order: Authentication happens first, then authorization
Common methods: Authentication – passwords, multi-factor authentication, biometrics; Authorization – roles, permissions
Analogy: Think of entering a high-security building. Authentication is like showing your ID at the entrance. Authorization is like having a specific keycard that allows you to access certain floors.
Together, authentication and authorization create a strong security system. By ensuring only verified users can access resources, and then limiting their actions based on permissions, you can protect sensitive data and functionality.
Types of types of Authentication with examples
different authentication types with examples:
- Password-based Authentication:
This is the classic login method you encounter everywhere. You provide a username and password to verify your identity.
Example: Logging in to your email account with your username (your email address) and password.
- Multi-factor Authentication (MFA):
MFA adds an extra layer of security by requiring two or more verification factors beyond just a password.
Example: Logging in to your bank account might require your password and a code sent to your phone via SMS or generated by an authentication app.
- Biometric Authentication:
This method uses your unique physical characteristics for identification.
Example: Unlocking your phone with your fingerprint or using facial recognition to access a secure application.
- Token-based Authentication:
This relies on a physical token, like a security key or smart card, to grant access. Often, these tokens generate unique codes that change frequently.
Example: Using a security key to log in to a work computer or a server, where the key physically plugs into a USB port and provides a unique code.
- Certificate-based Authentication:
This uses digital certificates issued by a trusted third party to verify the identity of a user or device. These certificates contain information about the user or device.
Example: Secure websites often use certificates to establish a secure connection between your browser and the website. The certificate verifies the website’s identity and ensures you’re not accidentally sending information to a fake website.
- Single Sign-On (SSO):
SSO allows you to log in to multiple applications with a single set of credentials. This is convenient but can be a security risk if compromised.
Example: Using your Google or Facebook login to access other websites or applications. This leverages the existing authentication of those platforms.
Happy Learning..
Leave a Reply